Network Graphs: Unterschied zwischen den Versionen
Aus exmediawiki
C.heck (Diskussion | Beiträge) |
C.heck (Diskussion | Beiträge) |
||
| Zeile 1: | Zeile 1: | ||
| + | by Yannick Westphal | ||
== Network Graphs == | == Network Graphs == | ||
Aktuelle Version vom 15. April 2020, 00:34 Uhr
by Yannick Westphal
Inhaltsverzeichnis
Network Graphs
Terms
Networks are systems whose underlying structure can be modeled mathematically as a graph and which have mechanisms for their organization. The graph consists of a series of elements (nodes) connected by connections (edges). A closed train of edges and nodes is called a net.
In mathematics, networks are often referred to as graphs, and the area of mathematics that concerns the study of graphs is referred to as graph theory. Graphs are mathematical structures used to study paired relationships between objects and entities.
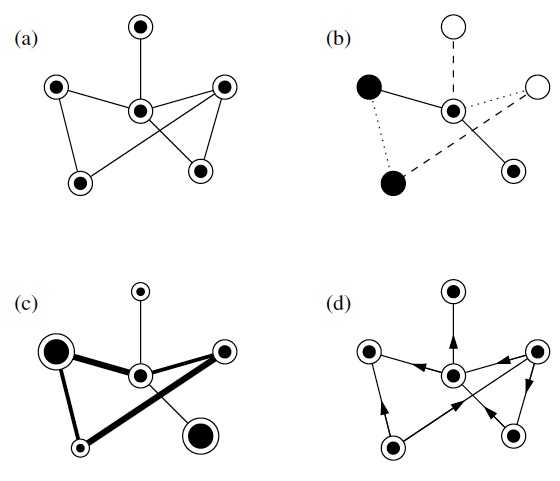
If one tries to model systems like the ones mentioned above, one quickly realizes that the simple network model with identical nodes and edges cannot describe important features of real networks. One problem is that the edges in this simplest network model are undirected. In the World Wide Web, for example, the links between the pages are directed. Just because I link from this page to the main page of Wikipedia doesn't mean that Wikipedia places a link from its main page back to this page. Since the edges are directed in this way, we have to use a directed network to describe the World Wide Web. In such a directed graph we usually draw the edges as arrows to indicate the direction, as shown below.
a. An undirected network.
b. An undirected network where the nodes and edges have different types, as indicated by their colors and line styles.
c. An undirected network where the nodes and edges have different size and weight.
d. A directed network.
History
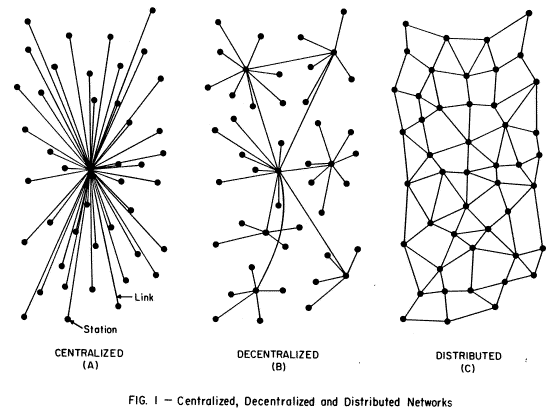
In 1964, RAND scientist Paul Baran drew this famous diagram that shows 3 possible network topologies and their levels of vulnerability in case of a nuclear attack. The distributed network was chosen for the military communication networks that set the foundation for the TCP/IP protocol which is at the core of the internet we use today.
Alex Galloway and Eugene Thacker defined protocols as all the conventional rules and standards that govern relationships within networks.
They argued that *“If networks are the structures that connect people, then protocols are the rules that make sure the connections actually work.”*
In today's world, where networks are becoming the leading model for power and control, the visualization of complex networks plays an important political role. In 2001, Josh Ons TheyRule.net, one of the pioneering websites to take on this role, was a network diagram writing tool that created diagrams of the most powerful American corporate executives and their members to identify potential conflicts of interest in the power classes.
For example VIS is a data visualization platform designed to assist investigative journalists, activists and others in mapping complex business or crime networks. "Our aim is to help investigators understand and explain corruption, organized crime and other wrongdoings and to translate complex narratives into simple, universal visual language." But there are a lot more.
According to the networked investigation model, the information puzzle can be solved by collecting and connecting the missing links. Data becomes currency and the network is the model that structures it. The larger the network we draw, the more possibilities we have to navigate within it.
NSA and other state and commercial espionage companies use exactly the same networked investigative model that helps *"good"* people fight corrupt politicians and organized crime, although their motives, goals, and especially their resources are very different.
Internet Protocols
DNS
The Domain Name System (DNS) is one of the most important services in many IP-based networks. Its main task is to answer requests for name resolution.
The DNS works similar to a directory enquiry service. The user knows the domain (the name of a computer on the Internet that people can remember) - for example khm.de. He sends this as a request to the Internet. The domain is then converted there by the DNS into the corresponding IP address for example, an IPv4 address of the form 194.95.160.32 or an IPv6 address and thus leads to the correct computer.
nslookup khm.de Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: khm.de Address: 194.95.160.32
The KHM ip Adress 194.95.160.32 belongs to one of the Networks owned by "Verein zur Foerderung eines Deutschen Forschungsnetzes e.V."
The IP-address 194.95.160.32 points to the KHM website, but the network is bigger. There are more services for example like mail. Therefore it is very likely that there are other servers or addresses as well. We will get back to that, but first some theory.
IPv4
IP Subnets
Standard local network ip Ranges
192.168.0.0/24 172.16.0.0/16 10.0.0.0/8
/24 means the number after the last point can be from 0 to 255. That means 192.168.0.1 to 192.168.0.255
192.168.0.1 192.168.0.2 192.168.0.3 192.168.0.4 ...
Possible Hosts connected to this network 254
On a /16 subnet the last two numbers can change from 0 to 255. That means for example 172.16.0.0 to 172.31.255.255.
That are 65534 addresses
/8 affects the last three numbers 10.0.0.0 to 10.255.255.255
16777214 addresses
Special address areas, such as the local ones shown above, are standardized according to RFC.
There are some other ranges that are reserved for certain purposes. According to this list, 622,199,809 of around 4.3 billion IPv4 addresses, or 14.5% of all possible IPv4 addresses, serve a specific purpose.
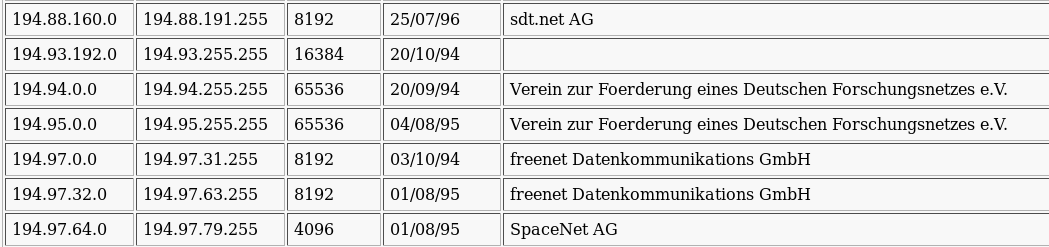
In the following table, you can find all major IP addresses blocks allocated for Germany. Most of these IP blocks are assigned for Internet providers and hosting companies.
Major IP Address Blocks For Germany
With this knowledge and tools like the following it is it possible to visualize the entire Internet as a network graph.
Tools
nmap
Nmap ("Network Mapper") is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts.
For reasons unknown, Hollywood has decided that Nmap is the tool to show whenever hacking scenes are needed. While Nmap had been used in some previous obscure movies, it was "The Matrix Reloaded" which really turned Nmap into a movie star!
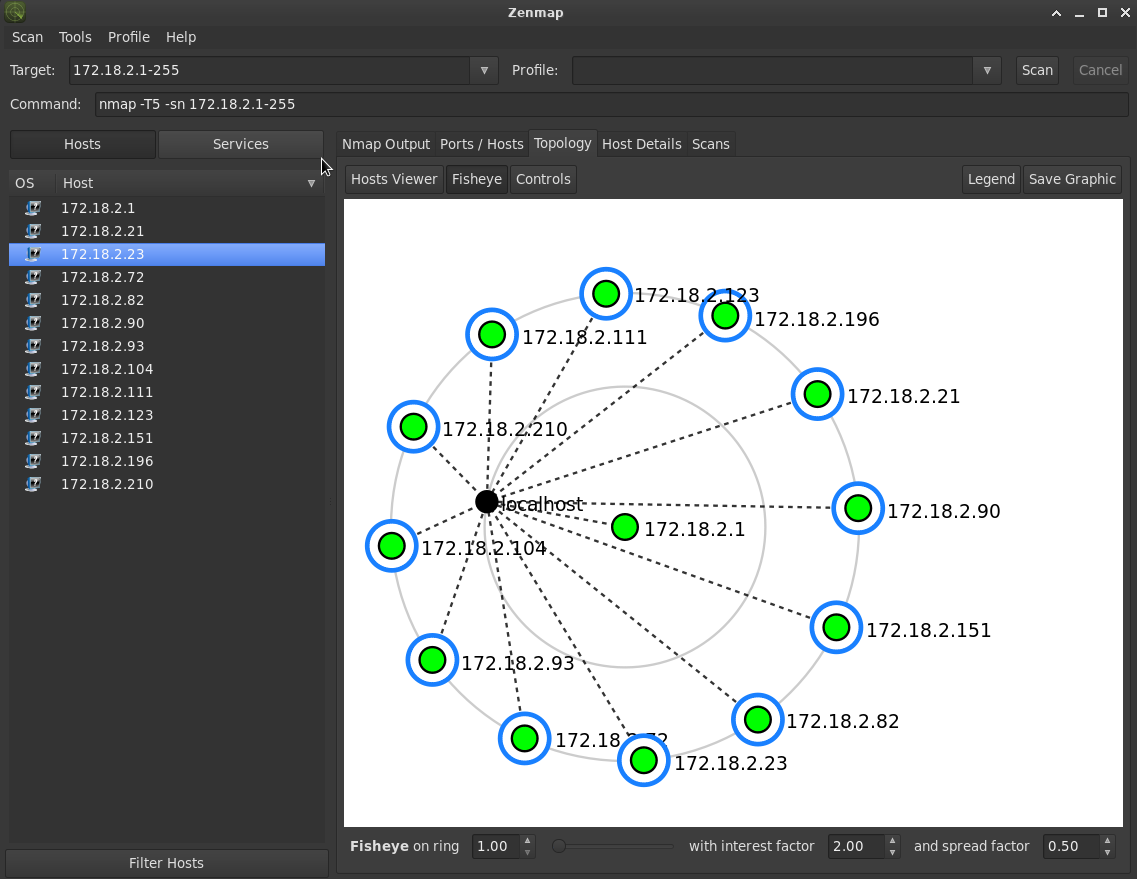
There is also a graphical tool, called zenmap. With this I have done a scan in the local exmedialab network.
We can see that 13 hosts are online in the local network.
masscan
We can scan a whole range relatively quickly with certain tools. One of them is [masscan](https://github.com/robertdavidgraham/masscan)
This is the fastest Internet port scanner. It can scan the entire Internet in under 6 minutes, transmitting 10 million packets per second.
As they write on their github page, scanning the entire internet is bad:
While useful for smaller, internal networks, the program is really designed with the entire Internet in mind. It might look something like this:
# 0.0.0.0/0 is like scanning adresses from 0.0.0.0 to 255.255.255.255. Thats about 4.294.967.294. # -p0-65535 means all possible ports, a scan for webservers only would just be port 80 and 443 masscan 0.0.0.0/0 -p0-65535
Scanning the entire Internet is bad. For one thing, parts of the Internet react badly to being scanned. For another thing, some sites track scans and add you to a ban list, which will get you firewalled from useful parts of the Internet.
Fortunately, there is one site that has already done just that for us. Like a normal search engine, you can search there for publicly available hosts on the Internet. For example, they can be filtered by region, open ports, or other metadata.
And because the KHM website is just behind another node in the internet, that can be addressed by the IP protocoll, we can find its IP-address on shodan, too.
DNS Reconnaissance
There are a few tools that try to identify networks of organizations from publicly available information, such as DNS database entries.
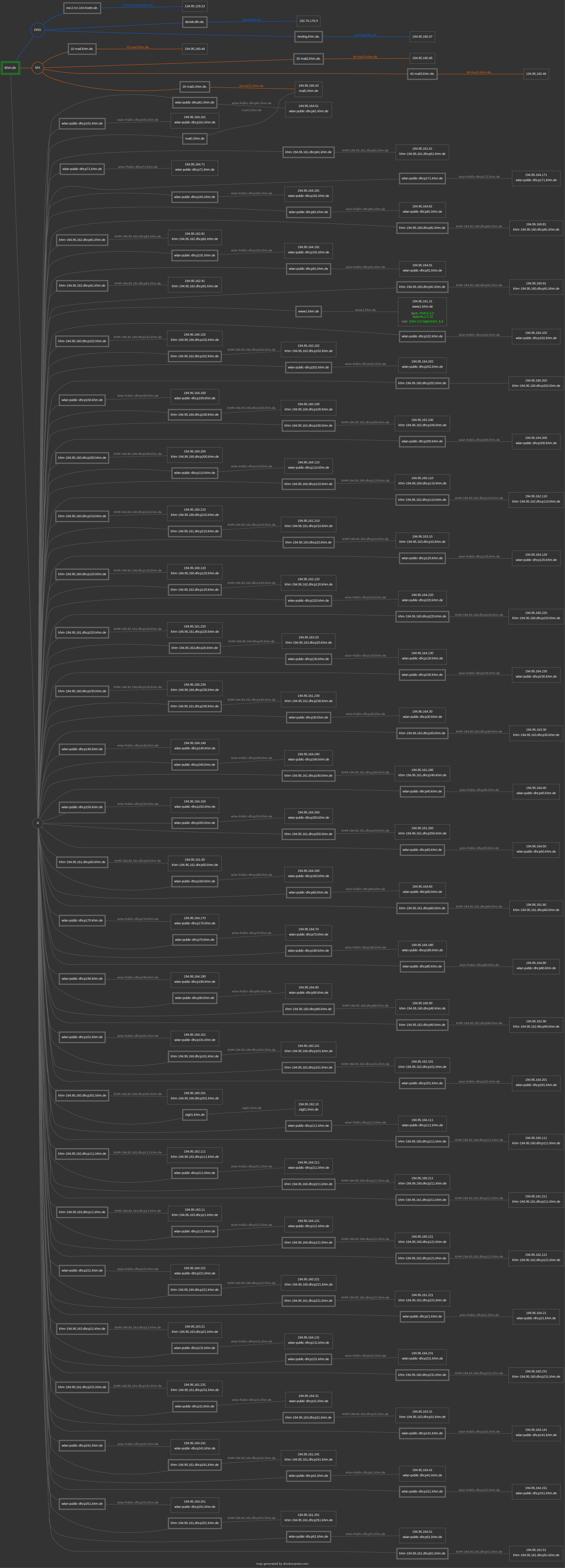
A nice website for this is DNSdumpster
As we can see, there are a lot more Addresses that belongs to the KHM network.
As we can see, another web server has been identified www1.khm.de.
Oooops...
Maltego
So far, we have only seen the purely technical possibilities of representing networks based on the IP protocol. There are some other tools, that can make more dimensions visible.
Maltego is a OSINT (Open Source Intelligence) tool. You have to register to use the community version.
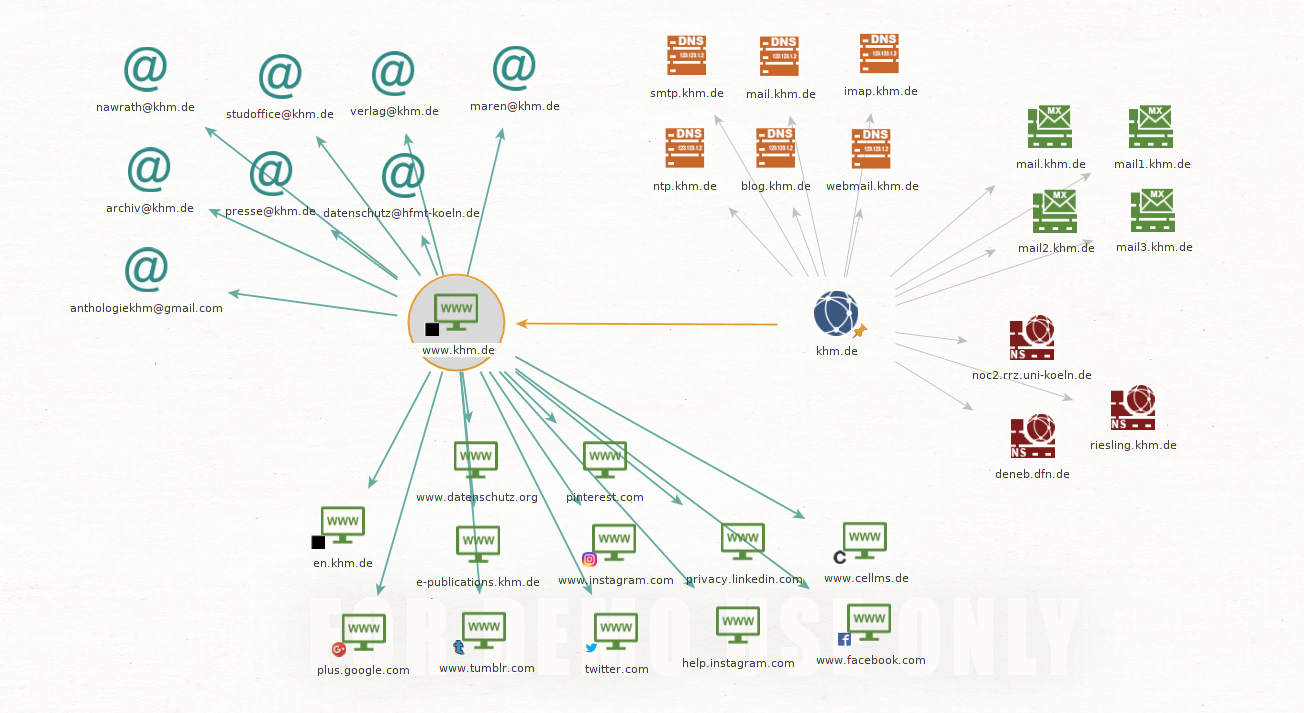
With maltego you can create graphs from collected and public information relatively quickly and easily. It can automatically crawl websites to search for links to other sites or email addresses, for example.
Now we can see how our network starts to get a new level. Through the email addresses, there are now more or less direct links with individual people.
Social Networks
There are some tools to visualize social media based networks.
Data
But what do we need to develop more complex network graphs? For example to see connections in larger organisations?
More Data
And indeed if we like, we can think of almost everything in terms of networks. Every place, institution, being, object, word, concept, cell or atom could be a node and as soon as we find any possible way to connect them with a few other nodes, we’ve got ourselves a network. The network is a very flexible and abstract model and can even allow us to overlay other networks and create super-networks and then run network mathematics on them to further analyse the inner workings of the complex emergent system we just discovered.
It is very likely, that most of the needed information is publicly available.
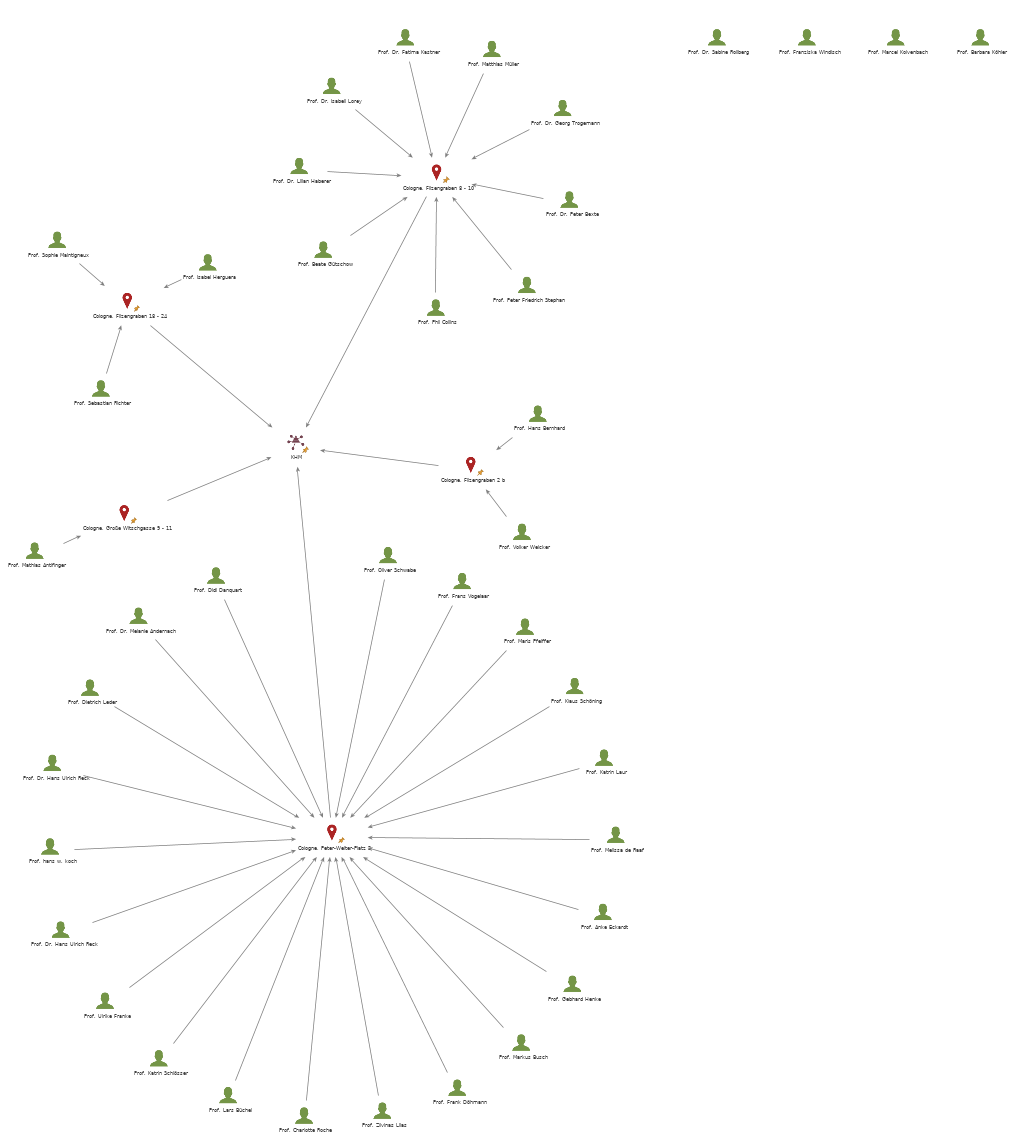
We can connect individuals with locations for example
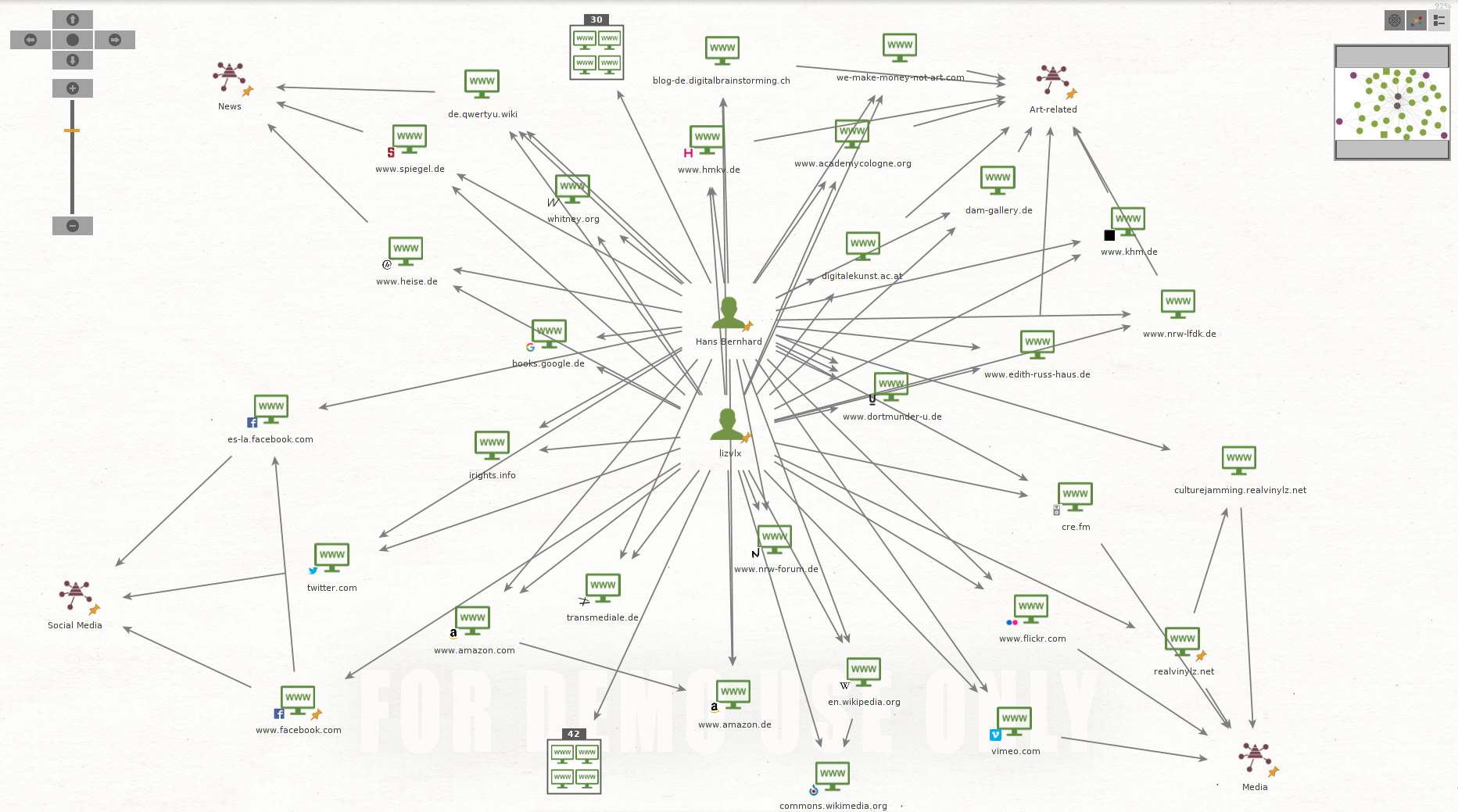
Although the network graph is now more person-centred, it still assumes that there is one organisation, in our case the KHM.
It becomes even more personal if we assume an Induviduum.
If you are interested in other tools that automatically search the web for usernames or terms, here are two examples.
Code
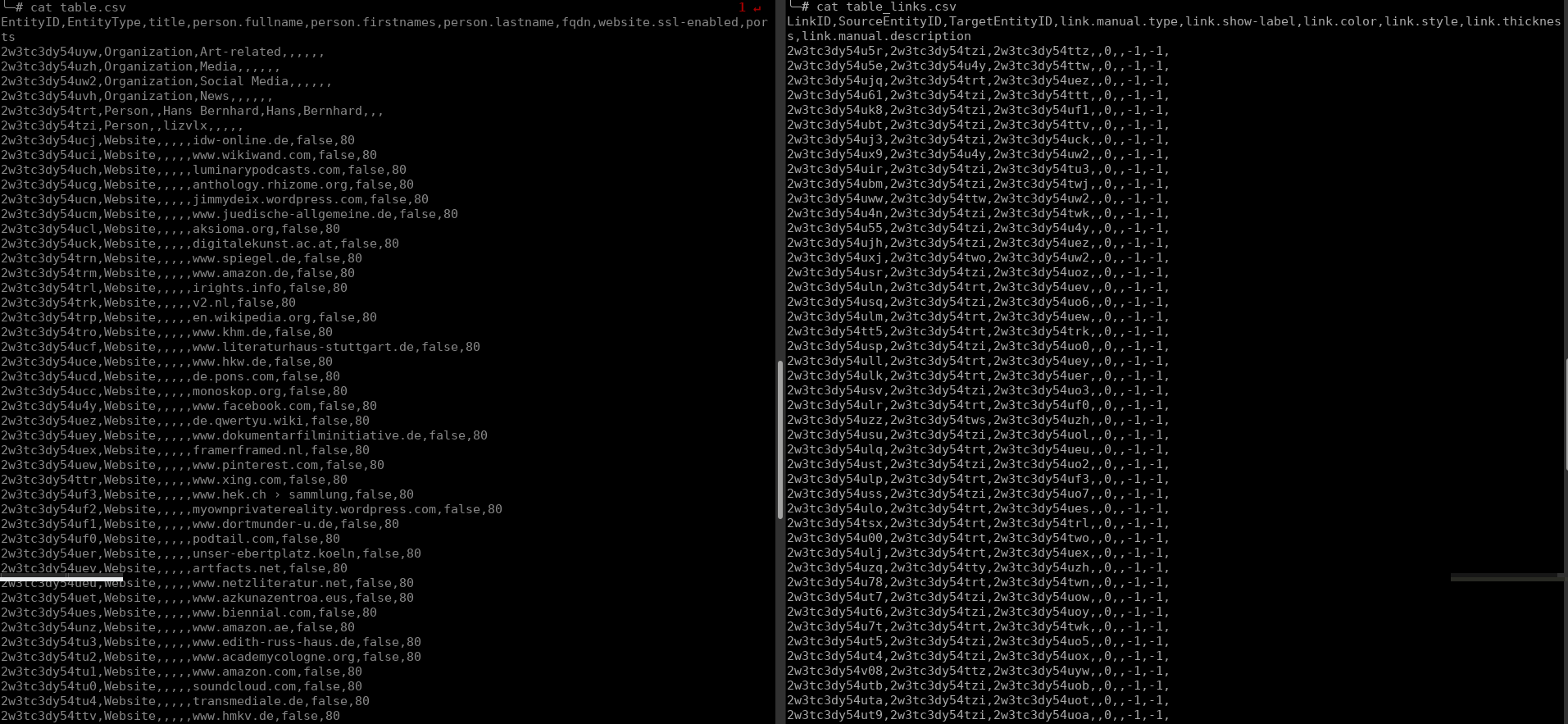
We can also view the whole network graph as data or table.
Therefore we can write further programs, which link the whole data arbitrarily.
>>> import pandas as pd
>>> data = pd.read_csv("table.csv")
>>> data.head()
EntityID EntityType title ... fqdn website.ssl-enabled ports
0 2w3tc3dy54uyw Organization Art-related ... NaN NaN NaN
1 2w3tc3dy54uzh Organization Media ... NaN NaN NaN
2 2w3tc3dy54uw2 Organization Social Media ... NaN NaN NaN
3 2w3tc3dy54uvh Organization News ... NaN NaN NaN
4 2w3tc3dy54trt Person NaN ... NaN NaN NaN
[5 rows x 9 columns]
Other
Lightbeam
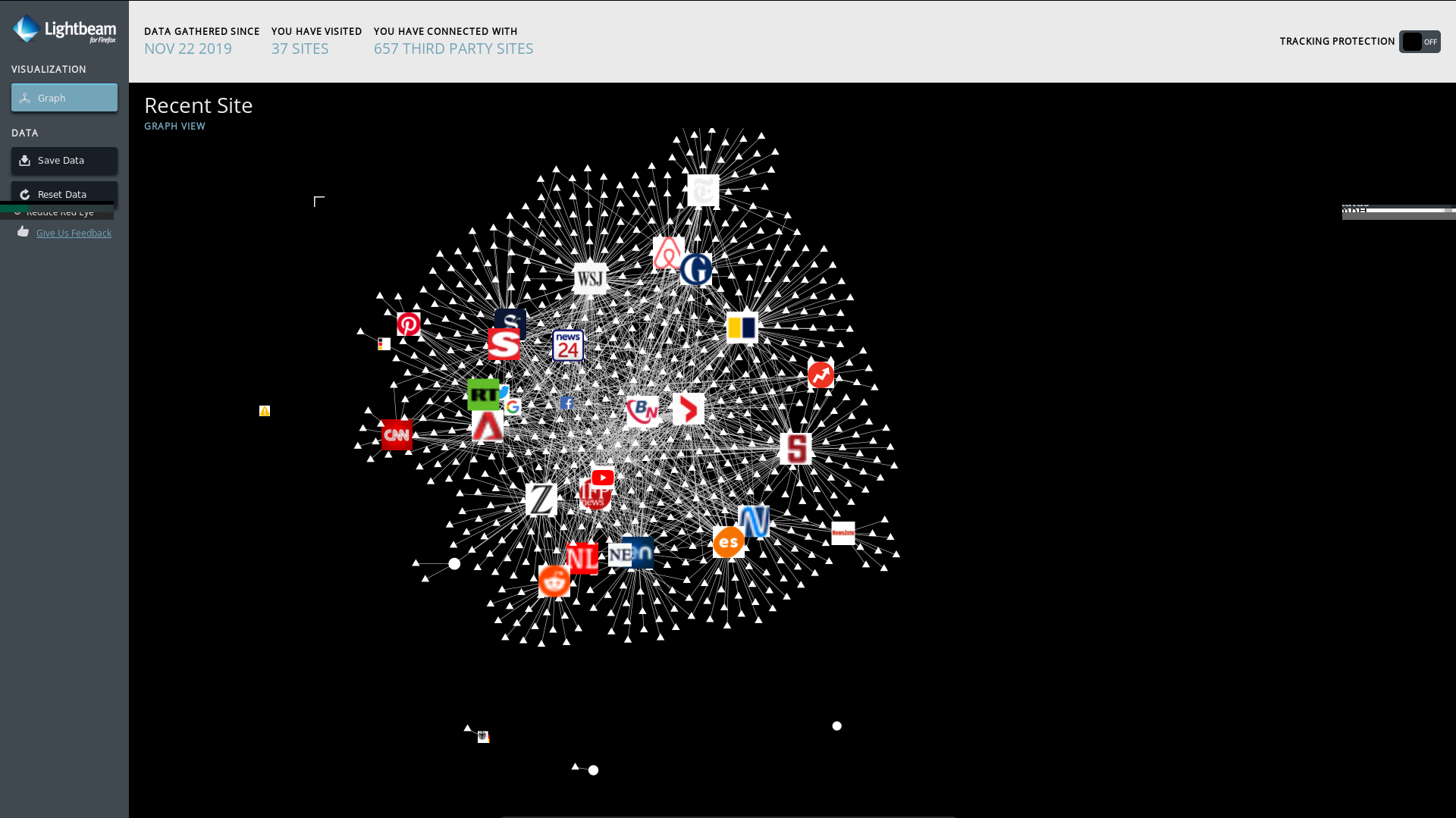
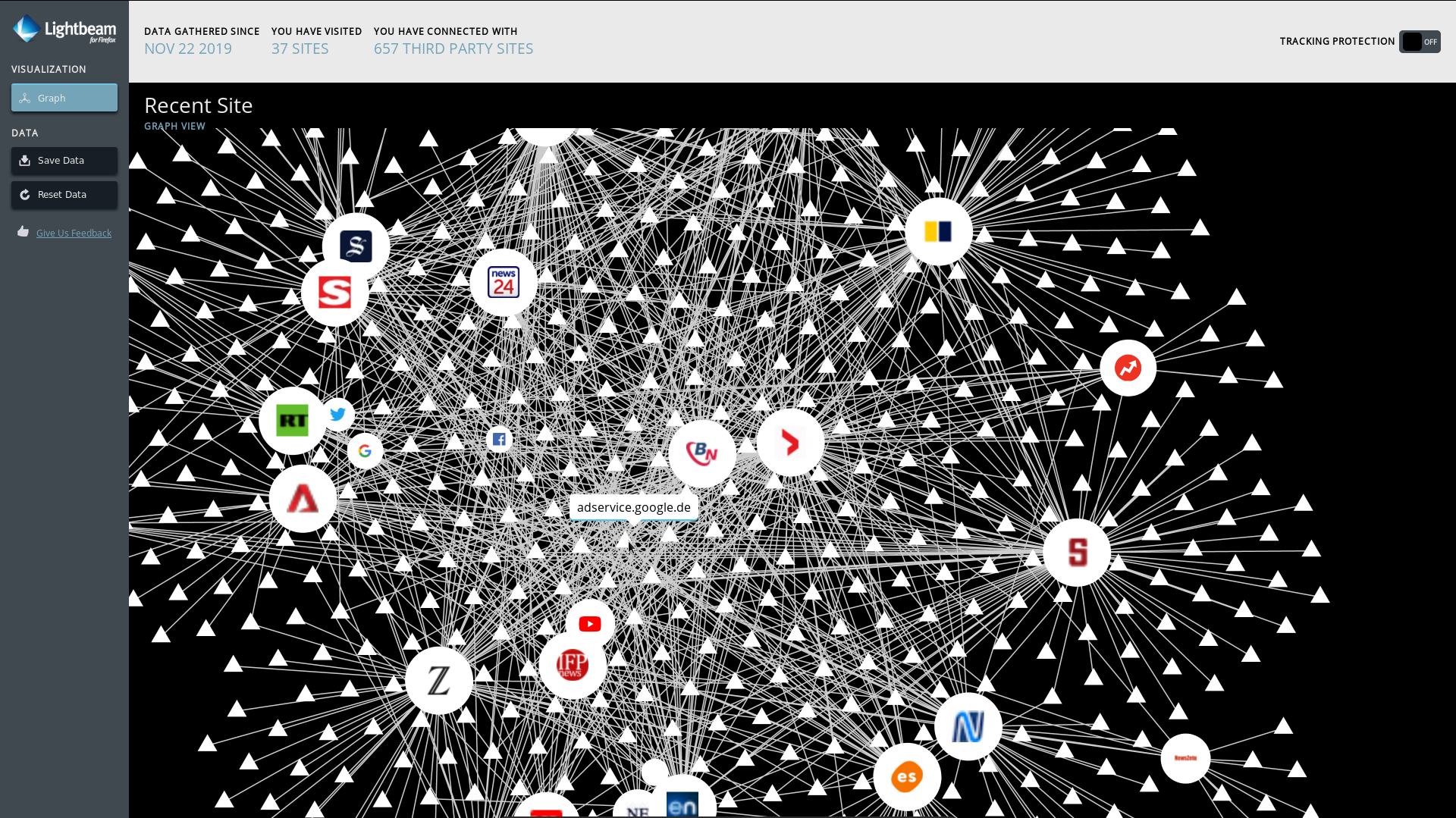
Lightbeam is a browser extension that uses interactive visualizations to show you the relationships between third parties and the sites you visit.
This is a visualisation of some worldwide popular news sites and their connections to ad and tracking services. Every little triangle is a ad or tracking server.
A very common example of a user tracking service is analytics.google.com. It's located near the center of this graph, because it's connected to almost every page.
Spiegel Mining
A cool example of reverse engineer social relationships with networks:
[Spiegel Mining](http://www.dkriesel.com/spiegelmining)
Some sources
[Twitter Ego Networks](https://towardsdatascience.com/generating-twitter-ego-networks-detecting-ego-communities-93897883d255)
[YouTube tutorial Maltego twitter](https://www.youtube.com/watch?v=wQV8QZLRO3U)
[Python programming](https://www.analyticsvidhya.com/blog/2018/04/introduction-to-graph-theory-network-analysis-python-codes/)
[Darknet Graph](https://incirtesiw.ga/dark-networks-social-network-analysis-of-dark-web-communities)
[Everything is a Network](https://visualisingadvocacy.org/node/739.html)
[Who follows who celebrities on twitter](https://graphics8.nytimes.com/images/2009/03/27/fashion/29twitter_1200.jpg)